JSON Web Token(缩写 JWT)基于JSON格式信息一种Token令牌,是目前最流行的跨域认证解决方案。
- JWT 的原理是,服务器认证以后,生成一个 JSON 对象,发回给用户。
- 此后,用户与服务端通信的时候,都要发回这个 JSON 对象。服务器完全只靠这个对象认定用户身份。为了防止用户篡改数据,服务器在生成这个对象的时候,会加上签名。
- 服务器就不保存任何 session 数据了,也就是说,服务器变成无状态了,从而比较容易实现扩展。
1. 依赖与配置文件
- 在
pom.xml中引入依赖:
1 | <dependency> |
- 用户信息从数据库中获取,在
application.yml配置文件中配置:
1 | server: |
2. 自定义Security策略
2.1 通过继承 WebSecurityConfigurerAdapter 实现自定义Security策略
1 | /** |
BCryptPasswordEncoder 解析器注入到容器
1 |
|
实现 UserDetailsService 接口,自定义逻辑
1 |
|
2.2 通过实现 AuthenticationProvider 自定义身份认证验证组件
1 |
|
实现 GrantedAuthority 存储权限和角色
1 | /** |
2.3 自定义JWT登录过滤器,继承 UsernamePasswordAuthenticationFilter
重写了其中的3个方法
attemptAuthentication:接收并解析用户凭证。successfulAuthentication:用户成功登录后被调用,我们在这个方法里生成token。unsuccessfulAuthentication:认证失败后被调用
1 |
|
自定义加密的签名key
1 | /** |
自定义全局API返回JSON数据对象
1 |
|
2.4 自定义JWT认证过滤器,继承 BasicAuthenticationFilter,重写doFilterInternal方法
从http头的Authorization 项读取token数据,然后用Jwts包提供的方法校验token的合法性。如果校验通过,就认为这是一个取得授权的合法请求。
1 |
|
2.5 通过实现 AuthenticationEntryPoint 自定义认证拦截器
1 |
|
3. 示例DEMO
sql
1 | DROP TABLE IF EXISTS `sys_user`; |
Java代码
1 | /** |
1 | <insert id="insertSysUser" keyProperty="id" keyColumn="id" useGeneratedKeys="true"> |
4. 测试
注册一个用户:
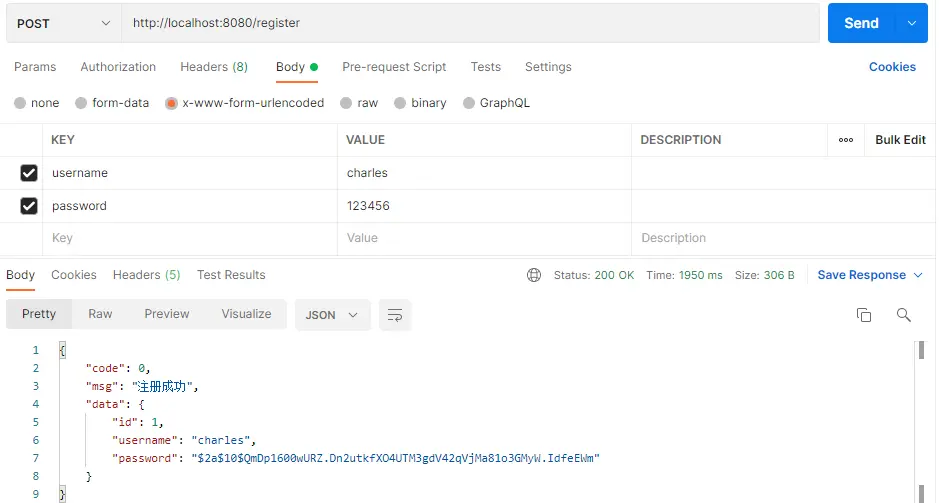
登录,返回Token:
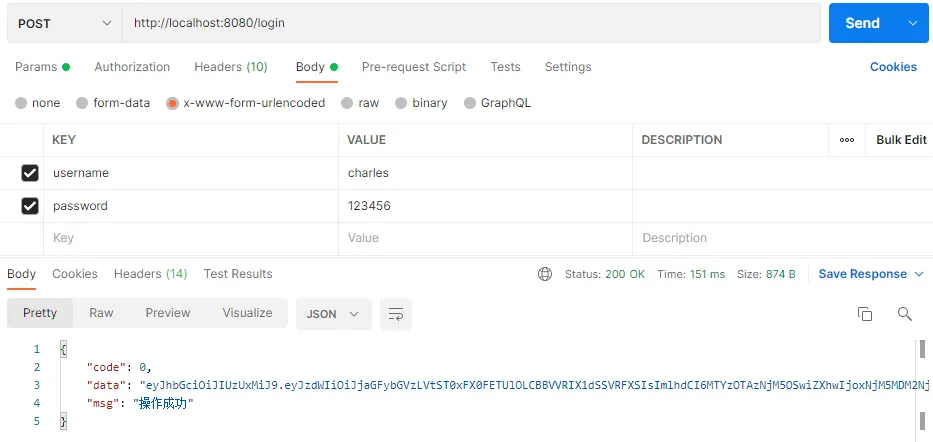
访问公开接口:
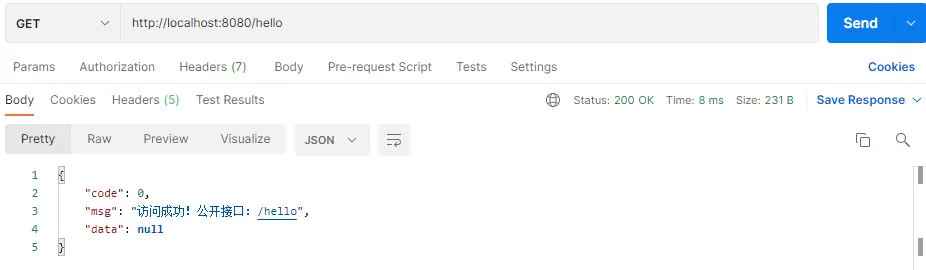
访问需要认证的接口,无权限返回403:
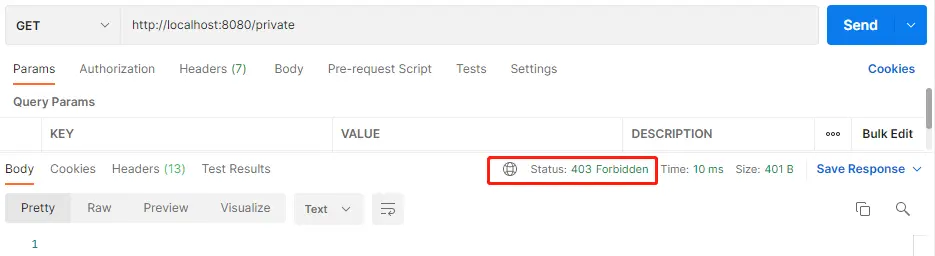
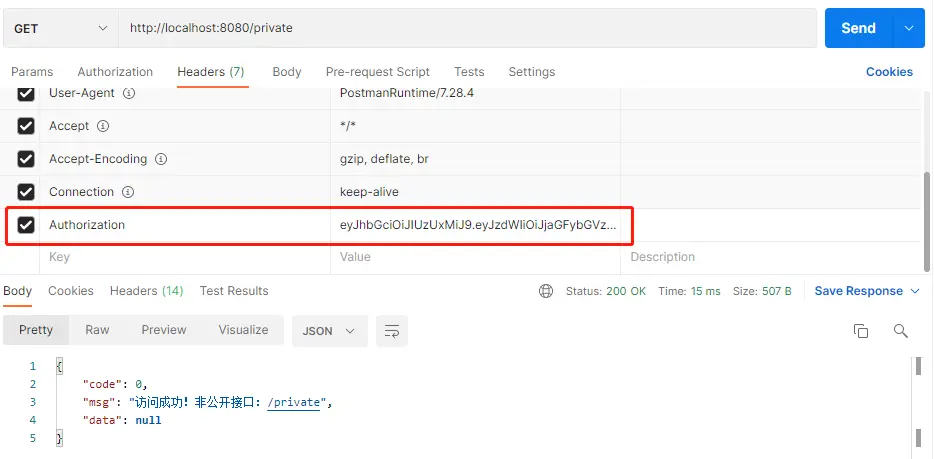
访问需要认证的接口,通过有效Token访问:
源码地址:https://github.com/chaooo/spring-security-jwt.git,
这里我将本文的登录认证逻辑放在github源码tag的V1.0中,防止后续修改后对不上。
原文链接: http://chaooo.github.io/2021/12/09/spring-security-jwt.html
版权声明: 转载请注明出处.