1. 开始之前
1.1 技术选型
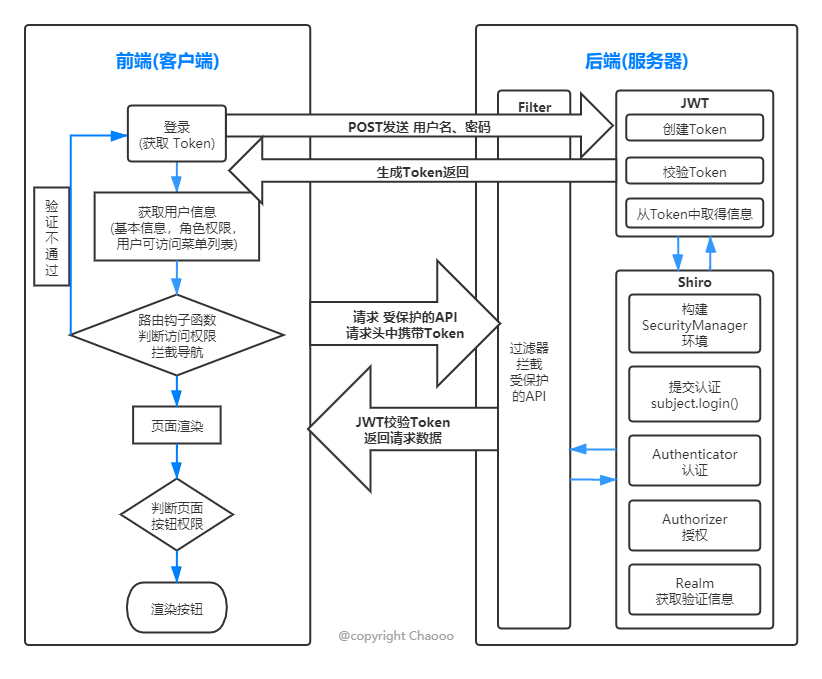
选用SpringBoot+Shiro+JWT实现登录认证,结合Redis服务实现token的续签,前端选用Vue动态构造路由及更细粒度的操作权限控制。
- 前后端分离项目中,我们一般采用的是无状态登录:服务端不保存任何客户端请求者信息,客户端需要自己携带着信息去访问服务端,并且携带的信息可以被服务端辨认。
- 而
Shiro默认的拦截跳转都是跳转url页面,拦截校验机制恰恰使用的session;而前后端分离后,后端并无权干涉页面跳转。 - 因此前后端分离项目中使用
Shiro就需要对其进行改造,我们可以在整合Shiro的基础上自定义登录校验,继续整合JWT(或者 oauth2.0 等),使其成为支持服务端无状态登录,即token登录。 - 在
Vue项目中,只需要根据登录用户的权限信息动态的加载路由列表就可以动态的构造出访问菜单。
1.2 整体流程
- 首次通过
post请求将用户名与密码到login进行登入,登录成功后返回token; - 每次请求,客户端需通过
header将token带回服务器做JWT Token的校验; - 服务端负责
token生命周期的刷新,用户权限的校验;
2. SpringBoot 整合 Shiro+JWT
这里贴出主要逻辑,源码请移步文章末尾获取。
- 数据表
1 | /** 系统用户表 */ |
- pom.xml
1 | <!-- JWT --> |
shiro配置类:构建securityManager环境,及配置shiroFilter并将jwtFilter添加进shiro的拦截器链中,放行登录注册请求。
1 |
|
- 自定义
Realm:继承AuthorizingRealm类,在其中实现登陆验证及权限获取的方法。
1 |
|
- 鉴权登录过滤器:继承
BasicHttpAuthenticationFilter类,该拦截器需要拦截所有请求除(除登陆、注册等请求),用于判断请求是否带有token,并获取token的值传递给shiro的登陆认证方法作为参数,用于获取token;
1 |
|
JwtToken
1 | public class JwtToken implements AuthenticationToken { |
JWT工具类:利用登陆信息生成token,根据token获取username,token验证等方法。
1 | public class JwtUtil { |
- MD5 加密工具类
1 | public class Md5Util { |
3. 注册与登录主要逻辑
这里只贴出主要逻辑,DAO和Mapper映射可查看源码,源码请移步文章末尾获取。
- 登录
Controller
1 |
|
- Service
1 | public interface SysService { |
- 统一接口返回格式
1 | public class ResponseVo<T> { |
注:这里的登录认证逻辑在
github源码tag的V1.0中,后续版本再加入Token续签和shiro前后端权限管理等。
源码地址: https://github.com/chaooo/springboot-vue-shiro.git
仅下载认证逻辑源码:git clone --branch V1.0 https://github.com/chaooo/springboot-vue-shiro.git
原文链接: http://chaooo.github.io/2020/01/18/authenticate-shiro-login.html
版权声明: 转载请注明出处.